Microsoft Azure Sources
Monitor Microsoft Azure Hosted Sources
This setup guide can be used for enabling data collection for all supported Bindplane Azure sources. Use the individual source documentation for specific LPU and connection configuration details.
Metrics are collected via the Azure REST API for most of the Bindplane Azure sources, with the exception of Azure SQL Database source. Azure SQL Database metrics are collected via JDBC from performance database tables.
Network Requirements
For all Bindplane Azure Sources except for SQL Database:
- Port: 443 (TCP) access to https://management.azure.com and https://login.windows.net
For Azure SQL Database:
- Port: 1433 (TCP) access to the database server IP address.
Microsoft Azure Data Collection Setup
Overview Reference on the Azure CLI:
Creating custom roles using the Azure CLI:
https://docs.microsoft.com/en-us/azure/role-based-access-control/custom-roles
Assigning roles using the Azure CLI:
https://docs.microsoft.com/en-us/azure/role-based-access-control/role-assignments-portal
Azure CLI
The following steps require the Azure CLI. Ensure you have it installed before continuing. To verify the Azure CLI has been installed, run the az help command. See: Microsoft Azure CLI Troubleshooting Guide for additional information.
Azure Cloud shell
There is an Azure Cloud Shell (CLI), which may be used to instead installing a local CLI. For more information: https://azure.microsoft.com/en-us/features/cloud-shell/
Subscription and Tenant IDs
Subscript and Tenant IDs are required for data collection from all the Azure Sources. One way to find those is using the Azure CLI
To obtain your Subscription ID (id ) Tenant ID (tenantId) Which is required for Source Configuration
Using the Azure CLI
az account list
The output should look similar to the following:
"cloudName": "AzureCloud",
"id": “<SUBSCRIPTION-ID>",
"isDefault": true,
"name": "Pay-As-You-Go",
"state": "Enabled",
"tenantId": “<TENANT-ID>",
"user": {
"name": "[email protected]",
"type": "user"
}
Create a custom RBAC role
This is an example of using the LPU's listed bellow. Use the source specific LPU for what you want to monitor.
To create a custom RBAC role, first you must create a file called azure.json that contains the following configuration. Replace Subscription ID with your ID that found in the above command.
{
"Name": "Blue Medora Microsoft Azure Monitoring",
"Description": "Monitor Microsoft Azure Environment by Blue Medora",
"Actions": [
"Microsoft.Compute/virtualMachines/*/read",
"Microsoft.Sql/servers/*/read",
"Microsoft.Storage/*/read",
"Microsoft.Insights/metrics/*/read",
"Microsoft.Authorization/*/read",
"Microsoft.Resources/subscriptions/resourceGroups/read"
],
"AssignableScopes": [
"/subscriptions/[Subscription ID]"
]
}
Next, create your custom RBAC role by running the following command:
az role definition create --role-definition azure.json
Client Secret: Create an Active Directory Service Principal (and AD App)
The secret is used for configuration of the Azure sources. This is an example of how to define this:
To create an AD Service Principal and assign a role to it, run the following command:
az ad sp create-for-rbac -n bindplane --role "Blue Medora Microsoft Azure Monitoring"
In the output you should find the required information.
Changing "bindplane" to a valid URI of "http://bindplane", which is the required format used for service principal names
Creating a role assignment under the scope of "/subscriptions/myId"
{
"appId": "myAppId",
"displayName": "bindplane",
"name": "http://bindplane",
"password": myPassword,
"tenant": "myTenantId"
}
Optional: To check the role assignment
You can execute the following command: NOTE: You may want to have jq installed to assist with JSON readability.
In the output, you should see "Microsoft Azure Monitoring in BindPlane" as the value for Definition.
az role assignment list | jq '.[].properties|{Name:.principalName,Definition:.roleDefinitionName}'
Client ID
After creating your AD Service Principal (and AD App), find your associated Client ID (appId) by running the following command:
NOTE: The appId in the output above is the Client ID
az ad sp list --filter="displayName eq 'bindplane'"
The output should look similar to the following:
[
{
"appId": "<CLIENT-ID>",
"displayName": "Network Watcher",
"objectId": "000af6c3-681a-4c76-982e-604a700d86d9",
"objectType": "ServicePrincipal",
"servicePrincipalNames": [
"7c33bfcb-8d33-48d6-8e60-dc6404003489"
]
Managing Azure LPUs using the CLI Script
Microsoft Azure Account Privileges
The Microsoft Azure Account being used to login, in either case below, requires that the account has administrator privileges
Prerequisite
- Install the jq command line tool
This is required for the script to run properly
How to acquire the Azure LPU CLI Script
Using the Cloud Shell
- Login to your Microsoft Azure Account
(The account must have administrator privileges) - Navigate to the Cloud Shell
2a. Use Bash instead of PowerShell with the Cloud Shell - Clone the repository from GitHub to a preferred directory
- Start using the Azure LPU CLI Script
Using a Local Shell
- Navigate to a command line that uses Bash
- Clone the repository from GitHub to a preferred directory
- Login to your Microsoft Azure account via the Azure CLI using the
az logincommand
(The account must have administrator privileges) - Start using the Azure LPU CLI Script
Cloning the repository from GitHub
First, navigate to the following web page using the provided link
Azure LPU CLINext, do the following:
- Click Clone or download
- Copy the URL to clone the repository using HTTPS
- Navigate to a preferred directory where the repository will be cloned to
- Using the 'git clone' command, clone the repository to the current directory
For more information on cloning a repository from GitHub, please click here
How to use the Azure LPU CLI Script
Understanding the Folder Structure
As per the image below, the main directory contains the scripts titled azure-create-lpu.sh and azure-delete-lpu.sh. Respectively, these scripts are used to create, or delete, an LPU. The output folder contains the individual.txt file and the master.txt file.
The individual.txt file contains individual LPU credentials for each BindPlane source, whereas master.txt contains a single LPU credential that is valid for all BindPlane sources. The template directory contains the master and individual folders. These contain JSON files that are used to create separate individual LPU credentials, or one master LPU credential that can be used for every Azure source in BindPlane.
Maintaining Credential Security
To maintain the privacy and security of the credentials, the following steps are recommended:
After creating the LPU, copy the contents of individual.txt and master.txt to a secure location (like your secret management system or password manager). Empty the master.txt and individual.txt files for the next run.
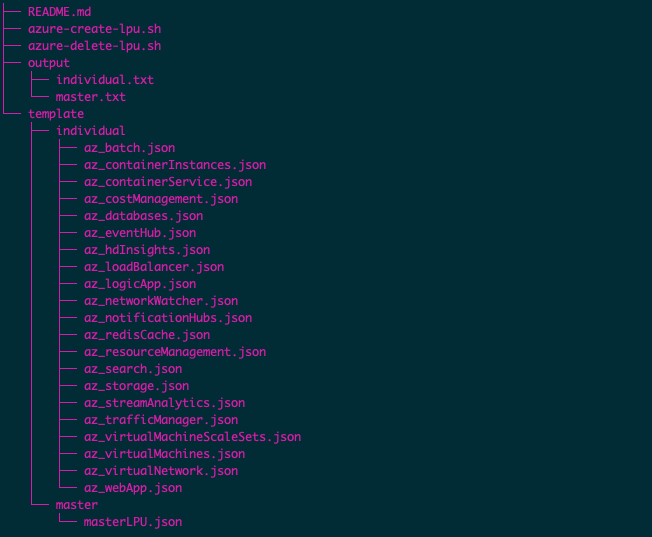
Azure LPU CLI Script Folder Structure
User Inputs Overview
Subscription ID:
The subscription ID associated with the Azure account
Password:
A user created password that will be associated with the LPU credentials that are created
Random Prefix:
A user created prefix that is used to identify the Custom Role that is being created.
Master or Individual LPU:
- Choosing Master creates a single LPU for all Azure services that are supported
- Choosing Individual creates multiple LPUs for each Azure service supported
How to create the Master LPU via the CLI Script
- To start, run the following command:
./azure-create-lpu.sh - Respond to the prompts that appear on-screen
2a. Input the Subscription ID
2b. Input a Password
2c. Input a Random Prefix for our role
2d. Choose to create the Master LPU by inputting a1
How to create an Individual LPU via the CLI Script
- To start, run the following command:
./azure-create-lpu.sh - Respond to the prompts that appear on-screen
2a. Input the Subscription ID
2b. Input a Password
2c. Input a Random Prefix for the role
2d. Choose to create the Individual LPU by inputting a2
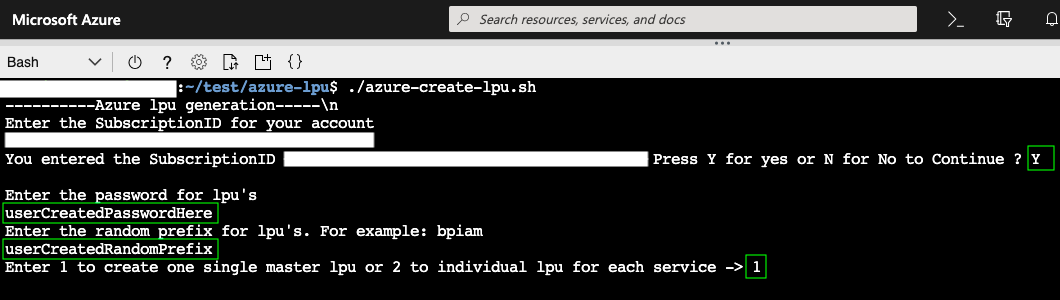
Creating the Master LPU
How to delete an Azure LPU via the CLI Script
- To start, run the following command:
./azure-delete-lpu.sh - Respond to the prompts that follow
2a. Input the Subscription ID
2b. Input the Random Prefix for the role
2c. Choose to delete the Individual LPU or Master LPU by inputting a1or2
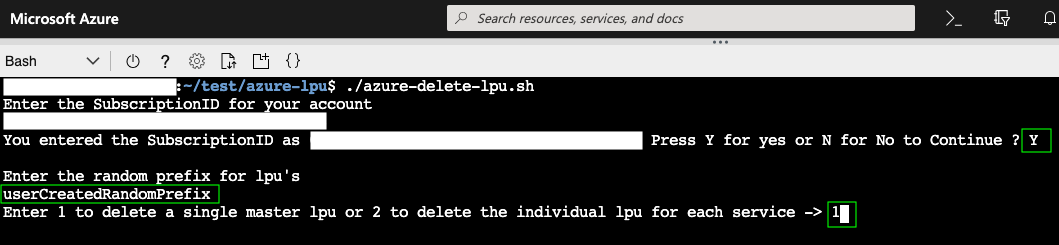
Deleting an Azure LPU
Updated over 4 years ago
