GCP Collector Deployments
Collectors can be deployed directly on GCP using a template. Here are the details and security requirements for that installation.
Deploying a collector to a Google Cloud Platform Project
- Login to the BindPlane account to be used
- Navigate to the Collectors page
- Click the Add Collector button located at the top right of the page
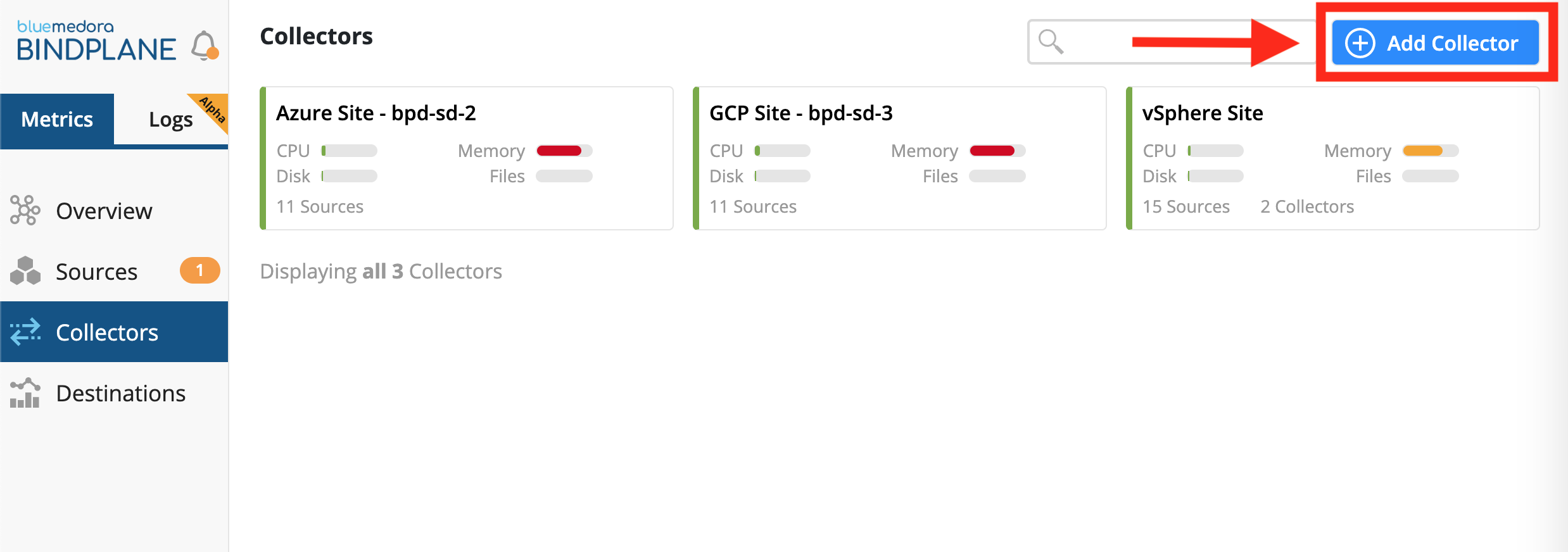
Collectors Page & Button to Add Collector
- For the platform, choose Google Cloud Platform

Choosing a platform to deploy a BindPlane Collector
- Copy the install command that is provided
- Click the Open Cloud Shell button located directly beneath the install command.
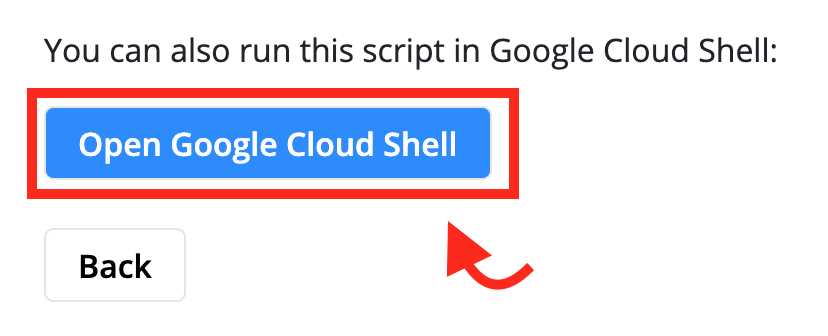
Button that Launches the Google Cloud Shell
- Check to make sure that project that has been set for the shell session is the correct project where the collector is supposed to be deployed.
- Paste and execute the install command, then follow the instructions as they appear.
Network Requirements
Once the collector is installed it only needs the following network access:
-
The ability to make outbound connections to all systems being monitored. This includes APIs for various cloud providers, if needed.
-
The ability to make outbound connections to
https://production.api.bindplane.bluemedora.com:443to send collection data back to BindPlane, as well as to retrieve configuration information.
IP Address Fluctuation
The IP address of
https://production.api.bindplane.bluemedora.com:443can change. The endpoint can exist anywhere within theus-east-1region on AWS.To retrieve a list of subnets that are covered, run the following commands:
wget https://ip-ranges.amazonaws.com/ip-ranges.json cat ip-ranges.json | jq '[.prefixes[]|select(.region=="us-east-1")]' | jq -r '.[].ip_prefix'> aws-useast1-ranges.txt
Least Privileged User
These are the minimum permissions needed to run the script to deploy the collector using the Google Cloud Deployment manager.
Collector Deployment LPU Permissions
compute.machineTypes.get
compute.machineTypes.list
compute.networks.list
compute.projects.get
compute.regions.list
compute.subnetworks.get
compute.subnetworks.list
compute.zones.list
container.deployments.get
deploymentmanager.deployments.create
deploymentmanager.deployments.get
deploymentmanager.deployments.list
deploymentmanager.manifests.get
deploymentmanager.manifests.list
deploymentmanager.operations.get
deploymentmanager.operations.list
deploymentmanager.resources.get
deploymentmanager.resources.list
resourcemanager.projects.get
resourcemanager.projects.list
Extremely Limited Least Privileged User
No attribute verification
This set of permissions will NOT allow the script to verify the attributes being passed into the script. Any misconfiguration will result in a failure of the deployment.
If all checks are removed from within the gcp_install.sh script, only the following permissions are required for the script to operate.
Collector Deployment Limited LPU Permissions
compute.subnetworks.get
compute.subnetworks.list
deploymentmanager.deployments.create
deploymentmanager.deployments.get
deploymentmanager.deployments.list
deploymentmanager.manifests.get
deploymentmanager.manifests.list
deploymentmanager.operations.get
deploymentmanager.operations.list
deploymentmanager.resources.get
deploymentmanager.resources.list
Creating a Google Cloud IAM Role
To create the Least Privileged User, or Limited LPU, a role needs to be created, using the permissions listed above.
- From the main menu within GCP, select the IAM & admin tab
- Click on the Roles option
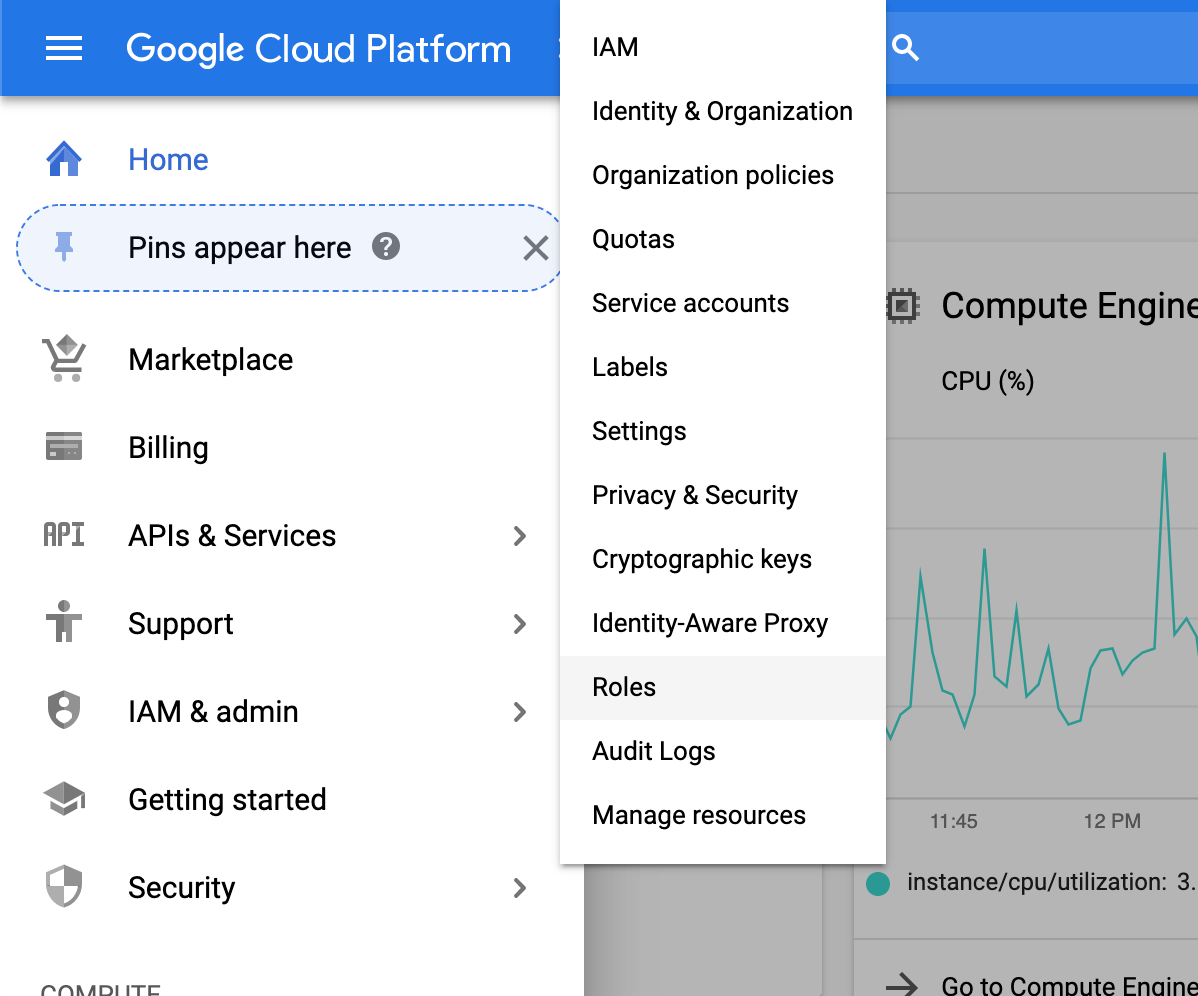
Steps 1 & 2
- Towards the top of the page, click on the + Create Role button
- Fill out the basic information for the form
- Click the + Add Permissions button
- Select the permissions that are required for the role.
- Click the Create button
Updated about 5 years ago
